Supernetworks, May Update
May 06, 2024 8:33 pm
Hello,
Welcome to the May update for Supernetworks! Please feel free to reach out for questions, suggestions, or comments, and join us on discord. We have been busy working on some new features while getting new hardware ready
April Saw Severe Router Vulnerabilities
Endless Router Bugs (@router_bugs)
April was a critical month for patches in the networking space. Critical flaws affected prolifically deployed firewall and vpn products in the enterprise with significant impact.
- PANOS: CVE-2024-3400: 🧨 CVSS10.0. Volexity uncovered game-over, critical, in-the-wild remote code execution against Palo Alto Network's GlobalProtect VPN. The vulnerability has affected PANOS since the 10.2 version release on 27 Feb 2022. Initially Palo Alto Networks believed they had a mitigating factor in that exploitation required the non-default threat detection feature to be enabled, but that was not the case, and all customers were actually affected. The underlying flaw was with an insecurity in Palo Alto's custom golang code for storing web session states. The bugs let attackers create files with unfiltered names that could be used to inject arbitrary shell commands.
- Cisco VPN: CVE-2024-20337 A Cisco Any Connect VPN Code Injection flaw was reported by Paul Yibelo. CVE-2024-20337. With user interaction attackers could break into Cisco VPNs when victims clicked attacker links to malicious web-pages. This may or may not be an initial network entry vector that is used by Sandworm to break into Cisco Routers and later install rootkits with CVE-2024-20359, by using a yet undetermined 🕵️ code injection flaw to run code on the routers and appliances.
- Netgear: 16 months ⌛ after a vulnerability was disclosed at Pwn2Own, NETGEAR has finally addressed a remote code execution flaw that affected closely related models. An overflow with HTTP Parsing in the SOAP services resulted in authentication bypass and code injection.
Hardware Update
- This month is a big step for us. We're announcing preorders for gear for running SPR. https://www.supernetworks.org/preorder.html
- In additional to the PI HAT put together a CM4 single-port board for WiFi. It's working great in testing and we're looking at enclosure design for it.
- We are testing our PI5 HATs which have arrived as of today
- Our big thing right now is finishing up some enclosure design and test prints
Software Development
- The next SPR release image will be based off of Ubuntu 24.04, Noble Numbat 🎉
- We have been improving the devices view to be easier to work with. In 0.3.11 users will be able to organize by device name, IP, recent DHCP time, groups, and tags, as well as search.
- SPR is based off of Docker images. We're continuing to monitor podman development to look at eventually making the switch. Recently docker compose broke the way they treated mounts of files, and we had to write a workaround as a fix for it. In general the software quality of docker could be better, but podman is still lacking some support we need for container networking.
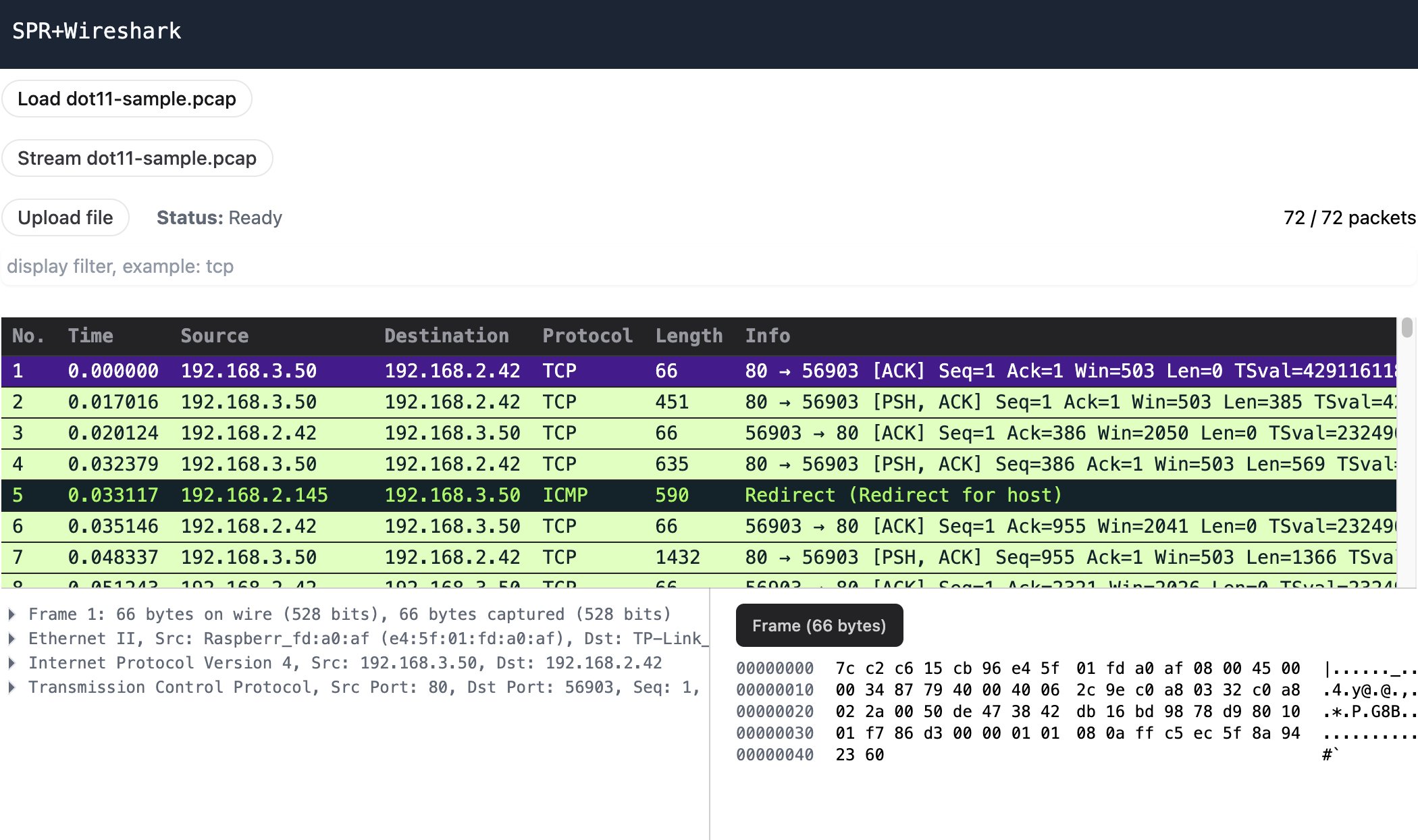
- We are testing out a new plugin, spr-wireshark, which will let users stream packets from there devices to the web browser. It uses a wasm build of wireshark, wiregasm, to parse packets in-browser and view them.
- Our focus for the upcoming release is making the install process a lot smoother without terminal access
Seeking Help with 3D Printing
- Join our team and collaborators on our enclosure design and print tests. We have a few ideas in progress.
- We're looking at SLS Nylon builds for their heat resistance and finish
Need Help? Have A Feature Idea?
- We love your bug reports and feature requests, keep sending them in
- We've had several requests to run SPR on some RISCV gear and other hardware. If you'd like to help out get in touch
Comments