Supernetworks: The April Update
Apr 02, 2024 2:07 am
Hello,
Welcome to our second newsletter.
In The News
At the end of February, a spyware boutique based in China named "I-Soon" had some information leak to the public about their malware offerings. Overall this vendor may not have top tier capabilities but we noted in a blog that they provide WiFi hardware implants for breaking into networks. These are used to exfiltrate data without traveling directly over a victim's outbound network traffic, where an attack might be detected.
https://www.supernetworks.org/pages/blog/isoon-wifi-exploitation-2024
Router Bugs
IWD
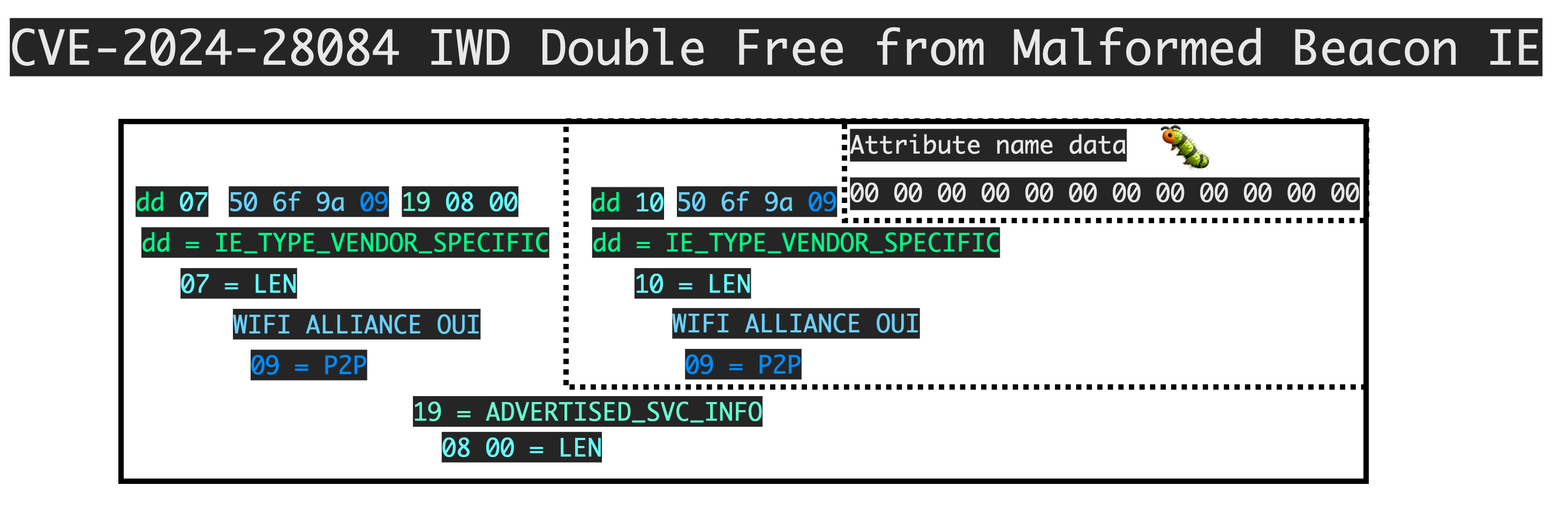
We reported, patched, and disclosed a preauthenticated, remote double-free vulnerability in iwd that came up as a result of some wifi fuzzing. The daemon is widely used by arch linux users as a replacement for wpa_supplicant. An attacker with radio proximity could trigger the bug to potentially gain arbitrary code execution. Overall this project needs more security testing and is not as battle hardened as hostapd/wpa_supplicant is.
Endless Router Bugs
We've made a new social media account, @router_bugs, which catalogues the Endless stream of router vulnerabilities as they pop up.

This round's top highlights:
GL.Inet's openwrt patches had login bypass due to Sql Injection https://twitter.com/gothburz/status/1765652411073368455
RaspAP had a series of Preauth and Post Auth Command Injection Flaws
https://dustri.org/b/carrot-disclosure.html
https://twitter.com/CVEnew/status/1768688489615479132
IOActive found Movistar Routers Running an ADB Debug Shell as Root
Hardware Focus
- Our PI5 Hat is now entering testing!
- Fill out the Order Interest Form to get early access
- It's a powered mPCI HAT that can provide more than the 5V/1A that the FP connector can do. It's designed to fit over the PI foundation's Active Cooler design.
Software Focus
- Apple Push Notification Support. For iOS users we've rolled out support for Push Notifications with alerts. As per Apple's requirements, a developer account is required to send these so we host a proxy in order to do so. The notifications are end to end encrypted and we do not store or process the metadata. If users do decide to Opt In to Push Notifications, we also allow users to disable the feature or specify their own APNs proxy server instead.
- The Tailscale Plugin is ready. You can install the spr-tailscale plugin now! It has a React UI and is now available with a simple URL based install. Compatible from versions 0.3.7 of SPR. It's an excellent demonstration of the capabilities SPR has for policy based networking. It fully takes advantage of our interface micro-segmentation capabilities to allow users to choose by policy which tailscale peers can access which SPR devices and vice versa, without an all-or-nothing decision.
- Have a plugin idea? Want help building a plugin? We'd love to help
- We keep a list of curated plugins: https://github.com/spr-networks/curated-super-plugins
- You asked, we listened. Special Groups are now Policies. The groups "wan", "dns", "lan" and the "lan_upstream" tag have been translated. These will be converted upon upgrading to v0.3.7.
How You Can Help
- We're looking for UI redesign ideas for the Devices view as well as PFW
- Submit your plugins for review or coding help
- Keep filing issues for features & bugs
- DM, email, or ask us for help
With Warm Regards,
The Supernetworks Team

