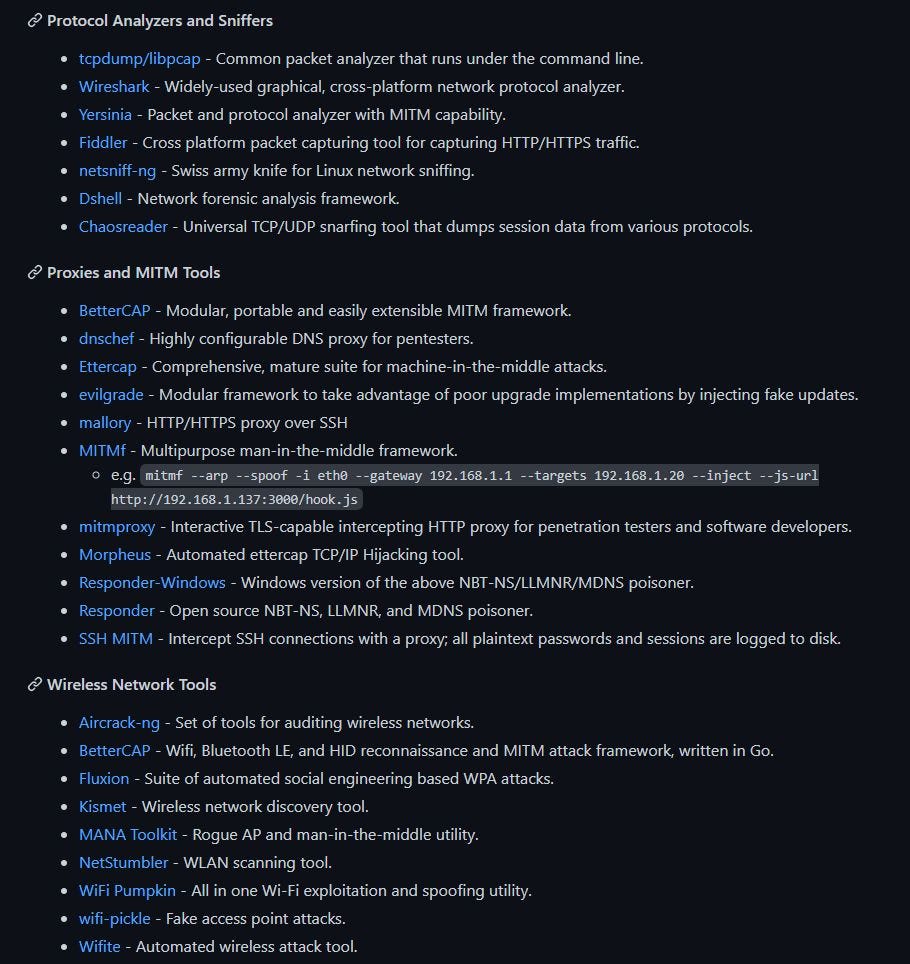
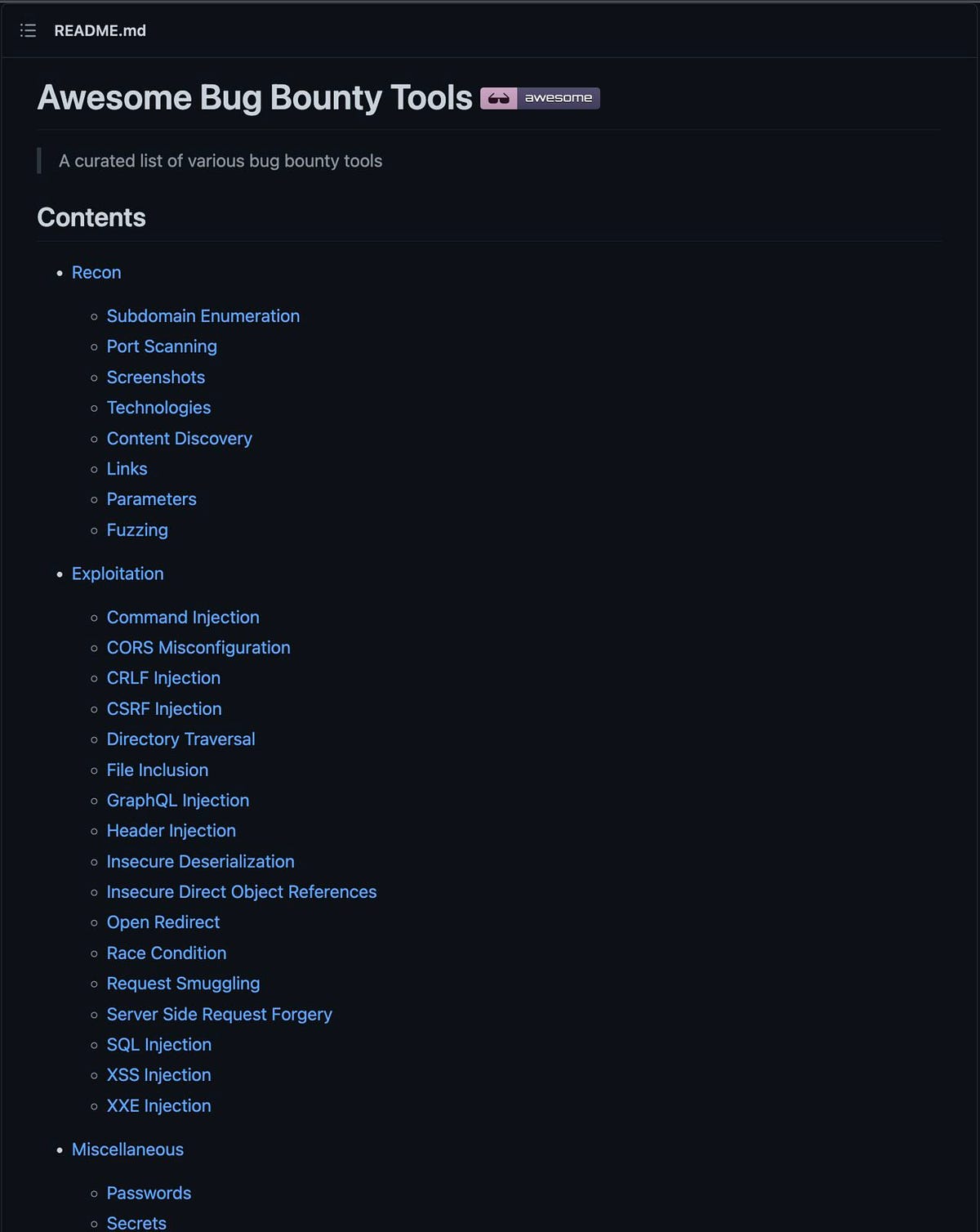
Photo by Tima Miroshnichenko from PexelsWhat is Threat Hunting?Threat Hunting refers to proactively looking for threats in your network. Threat Hunters actively search the network for any indication or sign of a threat or breach, whether known or unk...