May Cyber update II from the Office of Rob Kleeger
May 18, 2022 6:16 pm
,
I hope this email finds you and your loved ones safe, secure, and healthy. This year is moving quickly and appreciate the opportunity to be back in front of people again and getting back to the basics.
Let me know if you are interested in reconnecting!
All the best,
Rob Kleeger
1010101001010111010101100010100101010010101
Words of Wisdom:
“Life is a series of commas, not periods.”
~ Matthew McConaughey
CURRENT DATA SECURITY NEWS:
Law Firm Cyber Breach May Impact 23K, Including Financial Institution Client’s Customers
The cyberattack of Philadelphia midsize law firm Stevens & Lee has grown to include 23,066 people whose personal information was potentially compromised, including customers of the firm’s financial institution clients, according to public records. The new figure, revealed in notices to authorities last month, is a sharp increase from the 344 potentially impacted individuals reported by the 185-lawyer firm in December as a result of the June 2021 cyber attack.
This should be a reminder to all that law firms are magnets for cybercriminals, not just because of their wealth of client information, but because of their access to the personal information of clients’ customers, which may be sold on the dark web or used as to extort a firm by threatening to make the data public.
Stevens & Lee alerted state attorneys general and affected consumers to the breach in December. In a notice to authorities, the firm said an unauthorized third-party may have gained access to personal information of the firm’s customers, “or, as in your case, certain customers of our clients.”
In letters to affected individuals, the firm said, “You may not have heard of us but we are a law firm which assists financial institutions, one of which was a financial institution with which you had an account or which provided services in connection with loans or accounts you held.” The firm offered them free identity monitoring services. “While at this time we have no evidence that any information has been misused, and no conclusive evidence that your specific information was accessed, out of an abundance of caution we are providing you with free credit and identity theft protection services,” the firm wrote. The firm’s breach impacted people in multiple states.
Coca-Cola at the Center of Stormous Hacking Claims
The hacking group Stormous is attempting to sell over 100GB of stolen Coca-Cola data. The threat actors listed a cache of the data for sale on their leak site, asking 1.65 Bitcoin, currently converted to around $64,000.
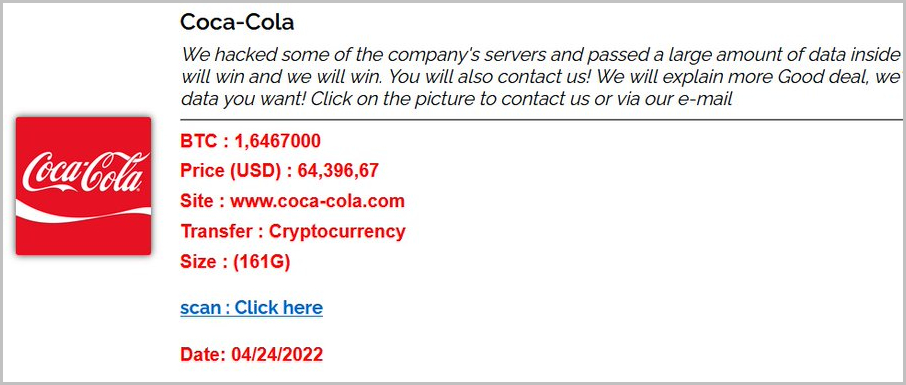 Coca-Cola listing on Stormous leak site
Coca-Cola listing on Stormous leak site
Among the files listed, there are compressed documents, text files with admin, emails, and passwords, account and payment ZIP archives, and other types of sensitive information.
This is the first time Stormous has posted a stolen data set. The attack promised denial-of-service, hacking, and leaking of software source code and client data.
Parker Hannifin reveals cyber-attack exposed sensitive employee data
Parker Hannifin, the Fortune 500 engineering giant, has revealed that the personal data of employees and their dependents may have been compromised after its networks were breached.
“Certain systems” were shut down after the company detected the incident on March 14, 2022, according to a press release issued on Friday (May 13).
An investigation subsequently discovered that an unauthorized third party had gained access to Parker Hannifin’s IT systems between March 11 and March 14.
Parker Hannifin said it began notifying potential victims, who include current and former employees, their dependents, and members of Parker’s Group Health Plans, on May 12.
79% of organizations have activated a disaster recovery response within the past 12 months
Zerto recently commissioned IDC to conduct a major ransomware and disaster preparedness survey, which revealed that 79% of respondents have activated a disaster recovery (DR) response within the past 12 months. 61% of these incidents were triggered by ransomware or other malware with 60% of organizations reporting they had experienced unrecoverable data during that same time—substantially more than the 43% response rate to the same question a year ago. In addition, the survey found that most organizations lack confidence in their current backup and DR solutions. Only 28% of respondents expressed 100% confidence in their backup system’s ability to recover data, and 29% have 100% confidence in their DR solution to recover data, though both numbers are higher than in the prior survey.
1010101001010111010101100010100101010010101
CURRENT LEGAL CASE UPDATES:
In re Actos End Payor Antitrust Litig.
This complex antitrust class action over alleged false patent claims made to the FDA regarding Takeda’s diabetes drug ACTOS was filed on December 31, 2013.
On March 18, 2015, the Court approved the Discovery Protocol that the parties had proposed, which called for the production of ESI in native format, together with metadata and coding fields, and for the parties to de-duplicate the ESI that is produced, but it stated nothing about producing only the most-inclusive emails in email threads.
Recently, NY Magistrate Judge Stewart D. Aaron ruled after observing that “Takeda’s exclusion of lesser included emails from production has resulted in the exclusion of the metadata associated with earlier emails in a chain”, ordered Takeda to produce “all responsive ESI to Plaintiffs, including earlier-in-time emails”. The Court recognized that "the production of earlier-in-time emails will cause some additional burden on Takeda, the Court finds that any additional burden is not undue since Takeda agreed to the Discovery Protocol and likely already has reviewed many of the emails at issue. Thus, Takeda shall produce all responsive ESI to Plaintiffs, including earlier-in-time emails.”
2022 WL 949798 (S.D.N.Y. 2022)Hacker sold cracked passwords for a living is now serving 4 years in prison
Glib Oleksandr Ivanov-Tolpintsev originally from Ukraine, who is now 28, was arrested in Poland late in 2020. He was extradited to the US the following year, first appearing in a Florida court on 07 September 2021, charged with “trafficking in unauthorized access devices, and trafficking in computer passwords.” In plain English, Tolpintsev was accused of operating what’s known as a botnet (short for robot network), which refers to a collection of other people’s computers that a cybercriminal can control remotely at will.
A botnet acts as a network of zombie computers ready to download instructions and carry them out without the permission, or even the knowledge, of their legitimate owners. Tolpintsev was also accused of using that botnet to crack passwords that he then sold on the dark web. The DOJ’s press release claims that he had a total of 700,000 compromised accounts for sale, including 8000 in the US state of Florida alone, which is presumably why Florida was chosen for his trial.
1010101001010111010101100010100101010010101
CYBER SECURITY TIPS OF THE MONTH:
KNOW YOUR ENVIRONMENT:
- INTERNAL ASSET DISCOVERY AND MANAGEMENT
You cannot protect what you do not know. You cannot restore your valuable data if you do not know where it is.
- KNOW YOUR INTERNET-EXPOSED ASSETS AND SERVICES
You need to determine whether any internal assets have ports or services that have unintentionally been exposed to the Internet. This typically occurs when servers or new endpoints are installed or configured with default settings and not properly locked down.
- SCRUTINIZE YOUR FIREWALL RULES
This will tell you exactly what internal connections you are allowing from the Internet, or vice versa. Validate that everything you have allowed in is legitimate and that you do not inadvertently have anything, such as RDP, allowed from the Internet. This firewall configuration audit should pertain to both outside-in and inside-out network communication.
- BASELINE NETWORK AND ENDPOINT ACTIVITY
Baselining helps identify anomalies by establishing known expected behavior in network and endpoint activity. Your baselines should provide an accurate picture of how the network typically operates.
- ADDRESSING VISIBILITY GAPS
Asset identification and discovery are vital to understanding the threat impact and risk within an environment. Once a basic understanding of your network landscape is gained, an important follow-on step is to capture and maintain logs.
- RESPONSE PLANNING
Organizations should always assume that a compromise is possible. Continuous monitoring can provide rapid detection of threats, but an efficient and well-executed Incident Response Plan in conjunction with Disaster Recovery (DR) or Business Continuity Plans (BCP) can significantly reduce the amount of time it takes to restore critical business functions. Therefore, you need to make sure you have a process in place to quickly respond to potential breaches.
1010101001010111010101100010100101010010101
Did you know that Digital4nx Group was recognized by Enterprise Security as one of the top ten digital forensics companies in 2022.
Being acknowledged as a leader in the industry is a great honor. In addition to the award, Enterprise Security featured Digital4nx Group and me in an article in their publication in print and online.
If you are an attorney who litigates, know one, or are a responsible business executive that's ass is on the line if a data breach occurs, I would love to have a call or introduction!
Please share the above information with those people or arrange an introduction. Look forward to seeing you in the flesh!
DON'T FORGET ABOUT US:
Digital4nx Group provides a blend of legal and technology services where we systematically identify, preserve, extract, analyze, and interpret digital evidence.
Our services are commonly used to:
- React and respond by providing litigation support services for plaintiffs or defendants, as well as providing expert testimony and consulting, both in and out of court.
- Proactively identify and provide insights on how to better secure your confidential data, technology, and compliance.
Cyber Security Services
Cyber incidents can be damaging to an organization, both in the short and long term. Digital4nx Group helps business leaders protect their “crown jewels” through reasonable, defensible, and cost-effective services... Before, During, and After a Data Incident! We offer a multi-disciplined approach to cyber services such as:
- Advanced “Ethical Hacking”
- Cyber Risk and Compliance Assessments
- Incident Response to Cyber Incidents or Data Breaches
- Cyber Security Awareness Training
- CISO-as-a-service


 If you are concerned about cyber attacks against you or your firm (
If you are concerned about cyber attacks against you or your firm (